44 aws best practices
Getting Started: Follow Security Best Practices as You Configure Your ... Best practices to help secure your AWS resources Create a strong password for your AWS resources. To help ensure that you protect your AWS resources, first set a strong... Use a group email alias with your AWS account. If for any reason you are unavailable to respond to an AWS notification... Enable ... aws.amazon.com › security-best-practicesLearn best practices for securing your AWS account and resources Aug 22, 2022 · For more information, see Security best practices in AWS CloudTrail. Use CloudTrail and CloudWatch in conjunction to monitor access key usage and receive alerts for unusual API calls. Activate resource-level logging (for example, at the instance or OS level) and Amazon S3 default bucket encryption .
aws.amazon.com › blogs › securityTop 10 security best practices for securing backups in AWS Jan 12, 2022 · Security is a shared responsibility between AWS and the customer. Customers have asked for ways to secure their backups in AWS. This post will guide you through a curated list of the top ten security best practices to secure your backup data and operations in AWS. While this blog post focuses on backup data and […]
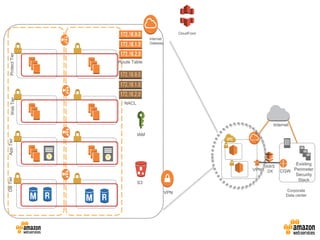
Aws best practices
AWS Security Group: Best Practices & Instructions - CoreStack Here are six best practices to assist in that process. Avoid the use of the "default" security group The "default" security group should not be used for active resources. This is because new AWS resources could be inadvertently assigned to it and thus allowed inappropriate access to confidential material. docs.aws.amazon.com › lambda › latestBest practices for working with AWS Lambda functions Best practices for using AWS Lambda. REPORT RequestId: 3604209a-e9a3-11e6-939a-754dd98c7be3 Duration: 12.34 ms Billed Duration: 100 ms Memory Size: 128 MB Max Memory Used: 18 MB AWS DevOps | Skaylink Als Marktführer im Bereich Cloud bringt AWS kontinuierlich neue Services sowie Best Practices und Leitfäden auf den Markt, um DevOps mit AWS zu implementieren. Als Advanced Consulting Partner hat Skaylink eine DevOps-Praxis entwickelt, die sowohl die Best Practices von AWS als auch unsere eigene jahrelange Erfahrung bei der Unterstützung von Kunden auf ihrer Cloud- und DevOps - Journey ...
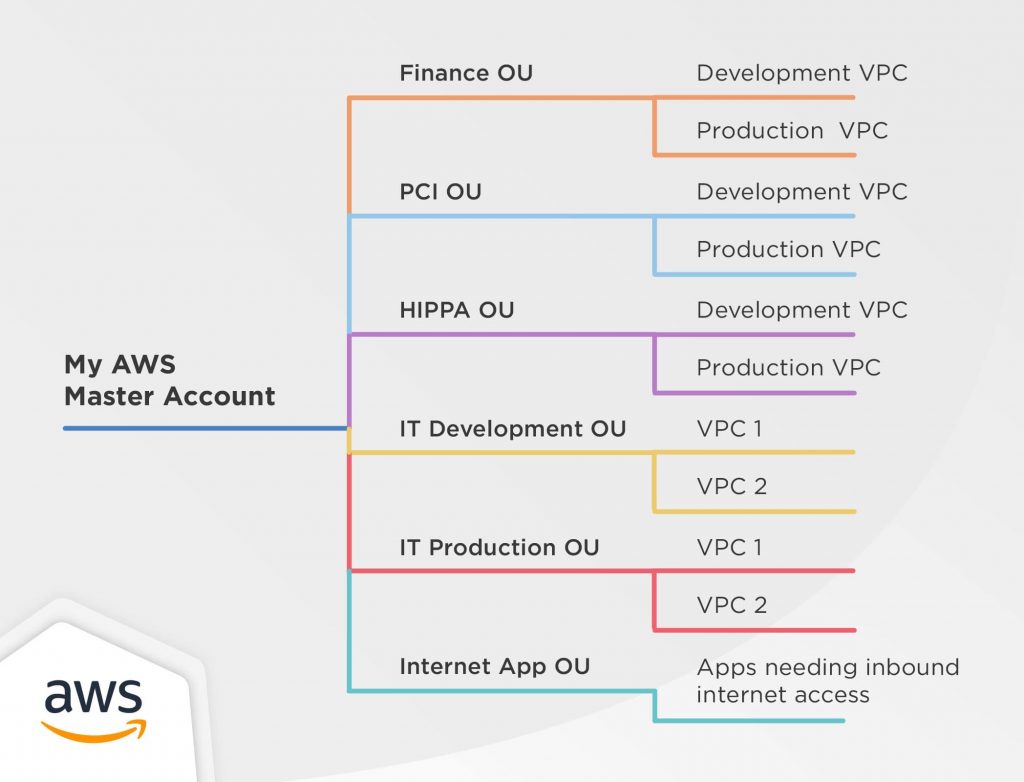
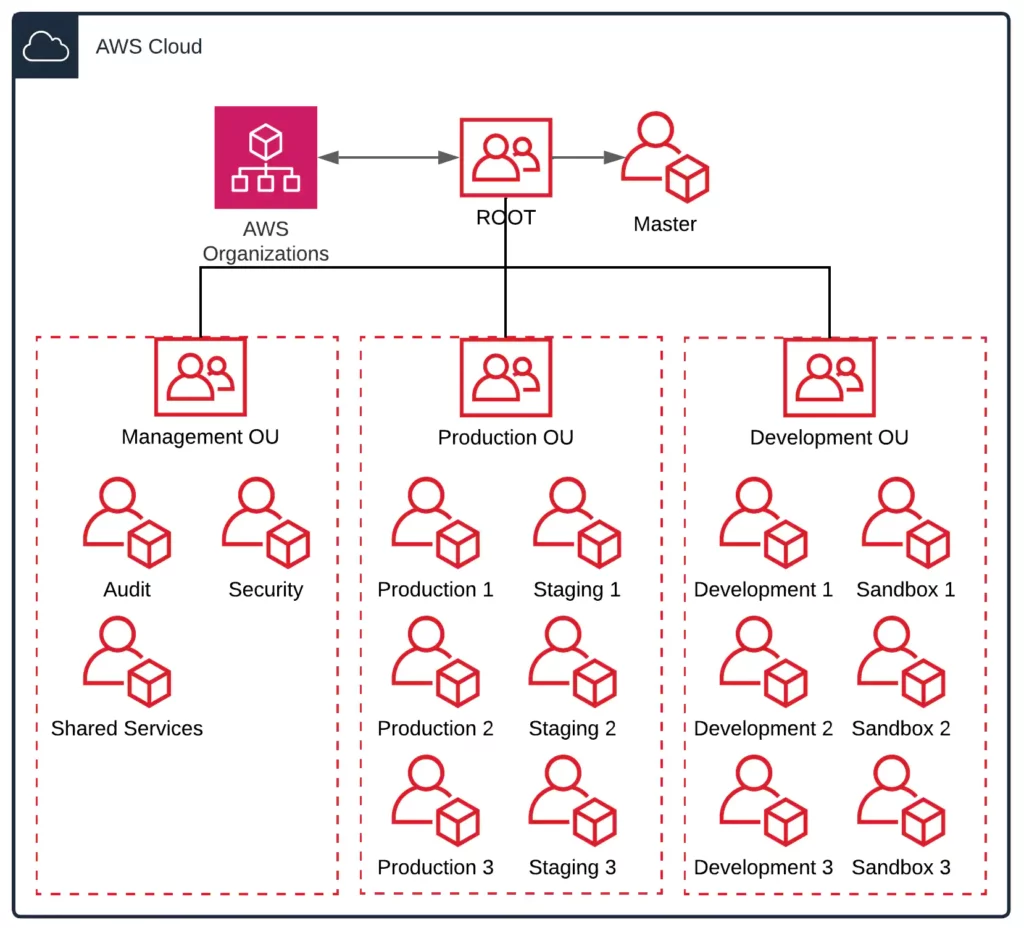
Aws best practices. Best practices for AWS Organizations - AWS Organizations Best practices for AWS Organizations - AWS Organizations AWS Documentation AWS Organizations User Guide Best practices for AWS Organizations PDF RSS We recommend that you follow these best practices when you create and operate your organization. Topics Best practices for the management account Best practices for member accounts 51 AWS Security Best Practices | McAfee Blog Below are some best practices around AWS database and data storage security: Ensure that no S3 Buckets are publicly readable/writeable unless required by the business. Turn on Redshift audit logging in order to support auditing and post-incident forensic investigations for a given database. Encrypt data stored in EBS as an added layer of security. Best Practices For Securing AWS EC2 Instances AWS regularly upgrades existing AMIs which further point to snapshots, permissions and boot volumes to use when an instance comes up. If you're using a custom built AMI, it's always a good practice to restrict the access to your own account. Secondly, only preserve your volumes after instance termination if there is a strong motivation to do so. 10 Best Practices for AWS Cost Optimization - Whizlabs Blog Among the prominent best practices for AWS cost optimization, it is essential to reflect on the optimization of network costs. The Trusted Advisor Idle Load Balancers check tool can help you find a report of load balancers with RequestCount lower than 100 in the last 7 days.
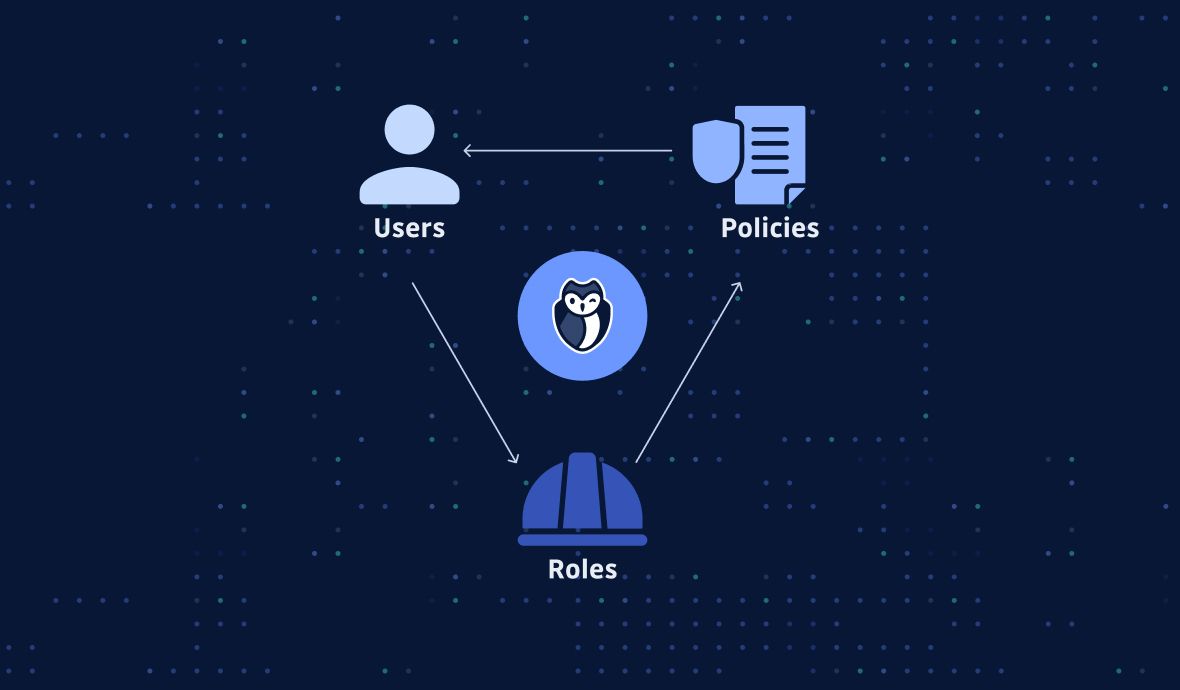
AWS S3 - Security Best Practices - Rently Engineering Blog So we need to follow the security best practices as discussed below. 1. Check for S3 bucket policies and block the public access. Assign S3 bucket policies and Access Control Lists (ACLs) for authenticated IAM users. S3 Bucket Policy. Block public access for S3 bucket. Block public access. PDF AWS Security Best Practices resources. All charges for activities performed by your IAM users are billed to your AWS account. As a best practice, we recommend that you create an IAM user even for yourself and that you do not use your AWS account credentials for everyday access to AWS. See Security Best Practices in IAM for more information. An introduction to AWS IAM best practices - SearchCloudComputing Here are some best practices to enhance IAM effectiveness and help avoid common security mistakes. Never use root credentials. A business might create a single AWS account with root credentials and then establish many different users and roles with other credentials. Establishing your best practice AWS environment Using a multi-account environment is an AWS best practice that offers several benefits: Rapid innovation with various requirements - You can allocate AWS accounts to different teams, projects, or products... Simplified billing - Using multiple AWS accounts simplifies how you allocate your AWS cost ...
Follow best practices | AWS Quick Starts - GitHub Pages If you're implementing Lambda-backed custom resources in your CloudFormation stack, review the best practices discussed in the AWS Support Knowledge Center. Linux Enable the -e flag at the top of all scripts (except user data) as follows: #!/bin/bash -e This will cause the script to exit with a non-zero exit code. AWS best practices | Edge for Private Cloud v4.19.01 - Apigee Docs Recommendation summary. Edge for Private Cloud v4.19.01. This section summarizes our best practices and provides our recommendations for using OPDK with AWS cloud. Cassandra is used as a backend and datastore for almost all the policies and is a critical part of the Apigee Edge runtime environment. This document focuses on optimizing Casssandra ... docs.aws.amazon.com › IAM › latestSecurity best practices in IAM - AWS Identity and Access ... Jul 14, 2022 · Use the root user to complete the tasks that only the root user can perform. For the complete list of these tasks, see Tasks that require root user credentials in the AWS General Reference. For more information, see Best practices to protect your account's root user in the AWS Account Management User Guide. Best practice - AWS Well-Architected Framework Best practice. Best practices are approaches, processes and methods that have been shown to lead to good outcomes. These are identified by looking at sets of outcomes and identifying common traits in those with successful outcomes. The reverse is also done, looking for traits that are associated with failures and then reversing them.
AWS Best Practices: five key approaches - Cloud Academy AWS Best Practices: Five Key Approaches to Get You Started 1. AWS Best Practices: protect your AWS credentials Your AWS account represents a business relationship between you and... 2. AWS Best Practices: secure your Applications Sometimes it is better to explain a concept with a picture or ...
aws/aws-eks-best-practices - GitHub GitHub - aws/aws-eks-best-practices: A best practices guide for day 2 operations, including operational excellence, security, reliability, performance efficiency, and cost optimization. aws / aws-eks-best-practices Public Notifications Fork 261 Star 1.1k Code Issues 25 Pull requests 5 Actions Projects 1 Security Insights master
AWS Tags Best Practices and AWS Tagging Strategies AWS Tags Best Practices While there isn't a perfect AWS tagging strategy that works for every organization, there are a few AWS tagging best practices that you should be familiar with. 1. Know how each AWS tag you create will be used AWS cites four categories for cost allocation tags: technical, business, security, and automation.
docs.aws.amazon.com › AmazonRDS › latestBest practices for Amazon RDS - Amazon Relational Database ... For information about best practices for working with Amazon RDS for Oracle, see Best practices for running Oracle database on Amazon Web Services. A 2020 AWS virtual workshop included a presentation on running production Oracle databases on Amazon RDS.
AWS VPC Security: 13 Best Practices [The 2022 Guide] - Hyperglance The best practice is to split your production, staging, and pre-production environments across different VPCs. Image courtesy of AWS 5. Use Security Groups To Control Resource Access It's vital that you factor in AWS Identity Access Management (IAM) when you're planning and setting up your VPC.
docs.aws.amazon.com › general › latestBest practices for managing AWS access keys - AWS General ... IAM Best Practices contains suggestions that help you secure your AWS resources with the AWS Identity and Access Management (IAM) service. The following topics provide guidance when you set up the AWS SDKs and the AWS CLI to use access keys:
13 AWS Security Best Practices - Check Point Software By following this AWS security best practices checklist, it is possible to improve the security of an AWS deployment. Identify Security Requirements 1. Define and Categorize Assets in AWS: It is impossible to secure systems that you don't know exist.
AWS Monitoring Tools and Best Practices: Monitor What Matters - NetApp Amazon Web Services (AWS) monitoring is a set of practices you can use to verify the security and performance of your AWS resources and data. These practices rely on various tools and services to collect, analyze, and present data insights. You can then use these insights to identify vulnerabilities and issues, predict performance, and optimize ...
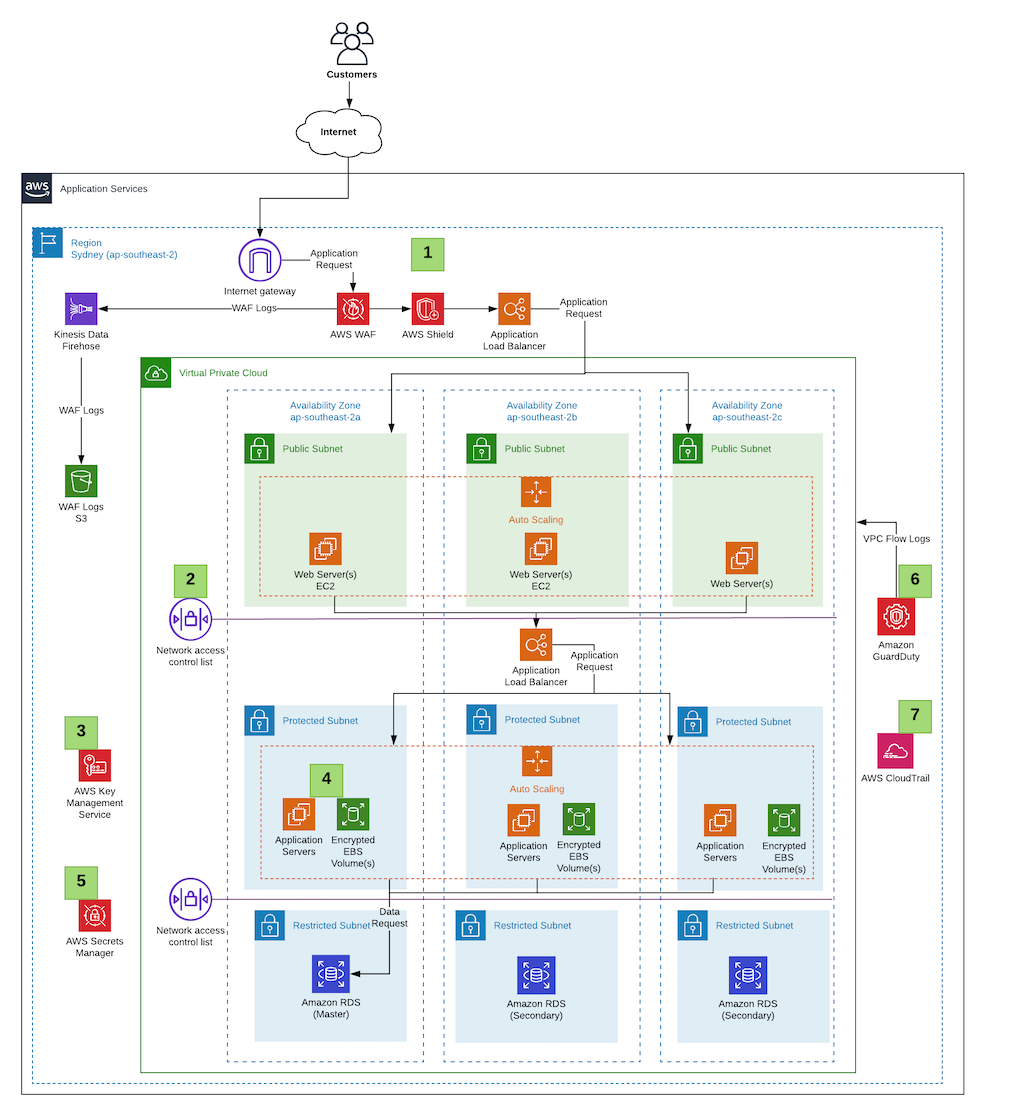
PDF Architecting for the loud Amazon Web Services - Architecting for the Cloud: AWS Best Practices Page 5 Design Principles The AWS Cloud includes many design patterns and architectural options that you can apply to a wide variety of use cases. Some key design principles of the AWS Cloud include scalability, disposable resources, automation, loose coupling managed services
8 AWS Cloud Security Best Practices You Need to Know Stay informed about the latest security updates and keep updating your AWS security best practices and store these policies on a shared drive accessible by all of your users so that everyone is on the same page. You can patch your AWS servers using a variety of third-party tools. You can also use AWS Systems Manager Patch Manager, which allows ...
9 AWS Security Best Practices - Alert Logic 9 AWS Security Best Practices. 1. Become Acquainted with the AWS Well-Architected Framework. While AWS isn't responsible for the security in your cloud environment, they do offer ample resources to help you protect your AWS workloads. If you're new to building on AWS, one of the first things you should read is the Well-Architected Framework.
PDF Amazon EMR Best Practices - d0.awsstatic.com The following scenarios explain three ways to optimize data migration from your current local storage location (data center) to AWS by fully utilizing your available throughput. Scenario 1: Moving Large Amounts of Data from HDFS (Data enter) to Amazon S3
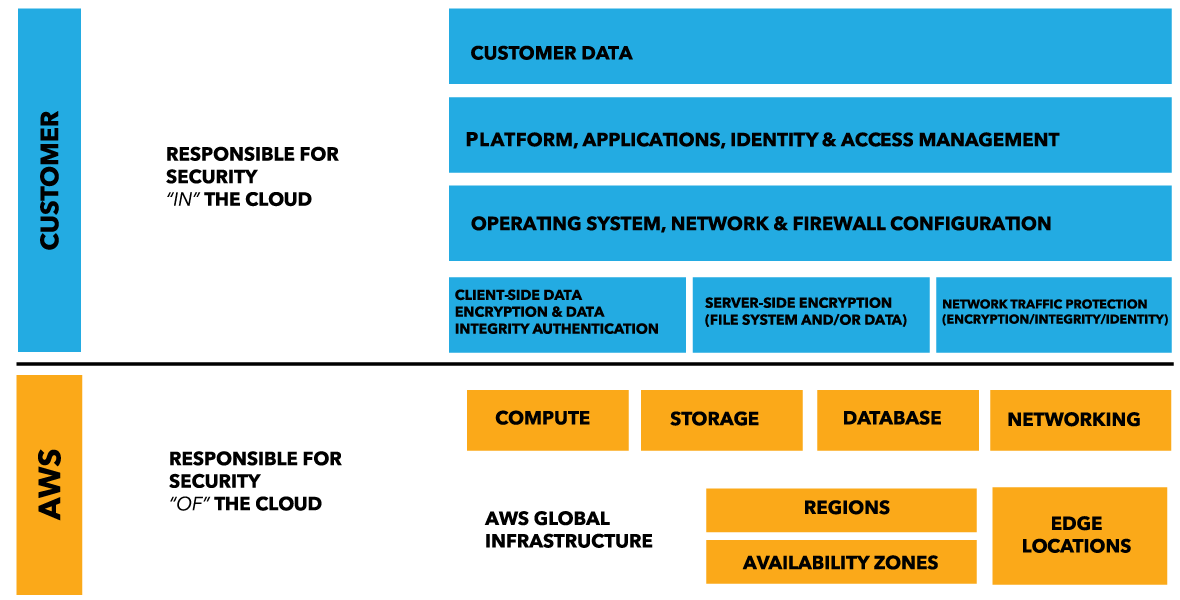
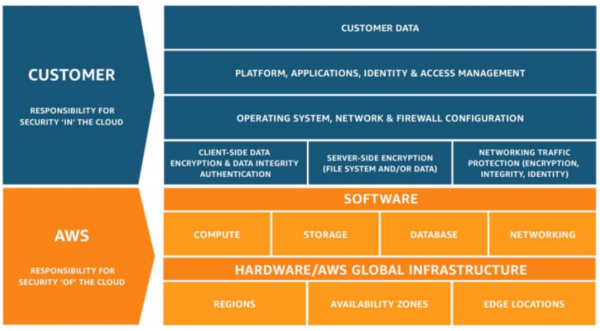
10 best practices for ensuring your AWS Cloud Security This article outlines the top 10 best practices for ensuring your AWS cloud security. The shared responsibility model. Let's first dive into the AWS shared responsibility model. Security and Compliance is shared between AWS and the customer. AWS operates, manages, and controls the security of the host operating system, the virtualization ...
AWS best practices: Amazon Elastic Compute Cloud - Site24x7 AWS best practices for EC2 instances. Though EC2 boasts built-in security and better control over servers as the infrastructure scales, it becomes laborious to manage the complete fleet of resources in AWS infrastructure. To obtain the maximum benefit and fulfill the requirements of your target workloads, let's check out the best practices for ...
docs.aws.amazon.com › security-best-practicesSecurity Best Practices for Amazon S3 Enable AWS Config. Several of the best practices listed in this topic suggest creating AWS Config rules. AWS Config enables you to assess, audit, and evaluate the configurations of your AWS resources.
21 AWS Security Groups Best Practices | McAfee Blog Download to learn about the AWS adoption trends, security challenges and best practices around AWS and applications deployed in AWS. Download Now 6) Outbound access: Restrict outbound access from ports to required entities only, such as specific ports or specific destinations.
AWS EBS Best Practices | Trend Micro AWS EBS Best Practices. Best practice rules for Amazon Elastic Block Store (EBS) Elastic Block Storage (EBS) volumes are block-level, durable storage devices that attach to your EC2 Instances. EBS Volumes can be used as your primary storage device for an EC2 instance or database, or for throughput-intensive systems requiring constant disk scans.
PDF AWS Key Management Service Best Practices - AWS Whitepaper AWS Key Management Service Best Practices AWS Whitepaper AWS KMS and IAM Policies Identity and Access Management The Identity and Access Management capability provides guidance on determining the controls for access management within AWS KMS to secure your infrastructure according to established best practices and internal policies.
AWS Security Best Practices - AWS Security Best Practices AWS Security Best Practices. Notice: This whitepaper has been archived. For the latest technical information on Security and Compliance, see .
AWS DevOps | Skaylink Als Marktführer im Bereich Cloud bringt AWS kontinuierlich neue Services sowie Best Practices und Leitfäden auf den Markt, um DevOps mit AWS zu implementieren. Als Advanced Consulting Partner hat Skaylink eine DevOps-Praxis entwickelt, die sowohl die Best Practices von AWS als auch unsere eigene jahrelange Erfahrung bei der Unterstützung von Kunden auf ihrer Cloud- und DevOps - Journey ...
docs.aws.amazon.com › lambda › latestBest practices for working with AWS Lambda functions Best practices for using AWS Lambda. REPORT RequestId: 3604209a-e9a3-11e6-939a-754dd98c7be3 Duration: 12.34 ms Billed Duration: 100 ms Memory Size: 128 MB Max Memory Used: 18 MB
AWS Security Group: Best Practices & Instructions - CoreStack Here are six best practices to assist in that process. Avoid the use of the "default" security group The "default" security group should not be used for active resources. This is because new AWS resources could be inadvertently assigned to it and thus allowed inappropriate access to confidential material.






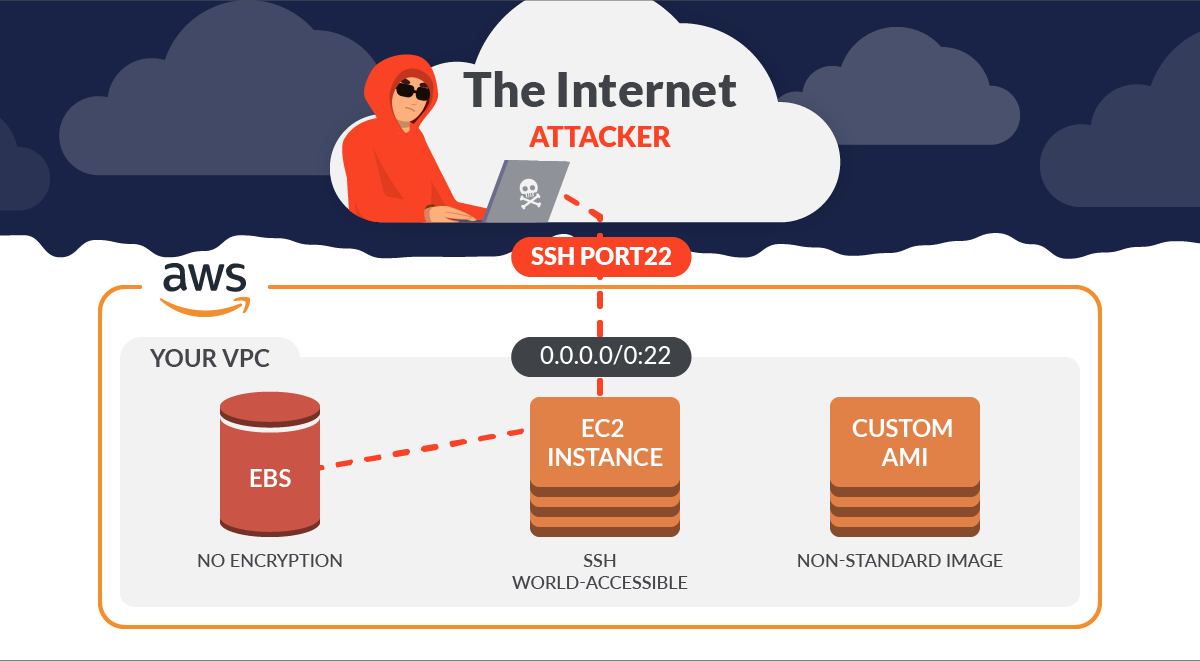



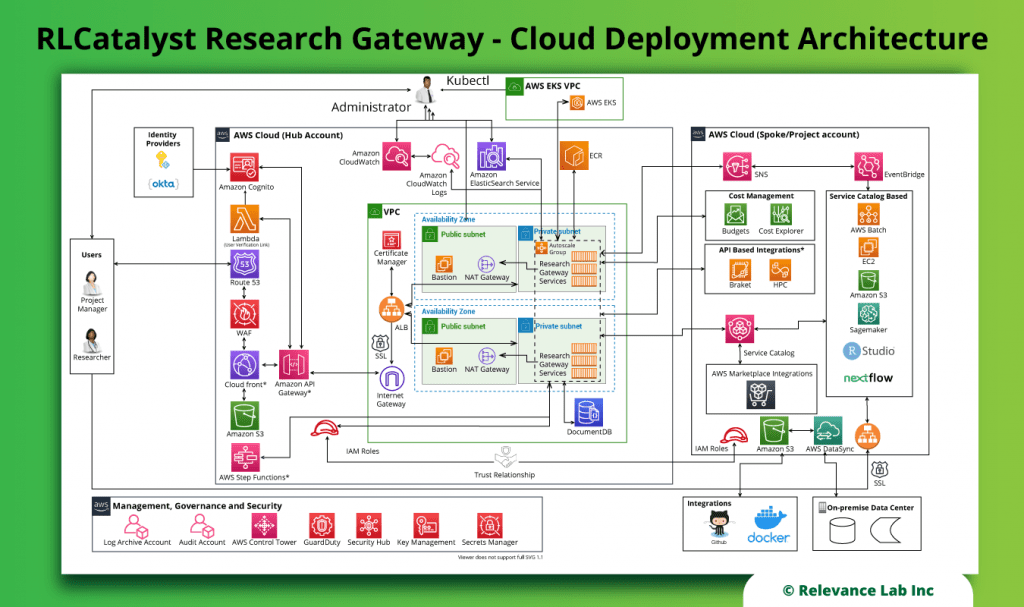

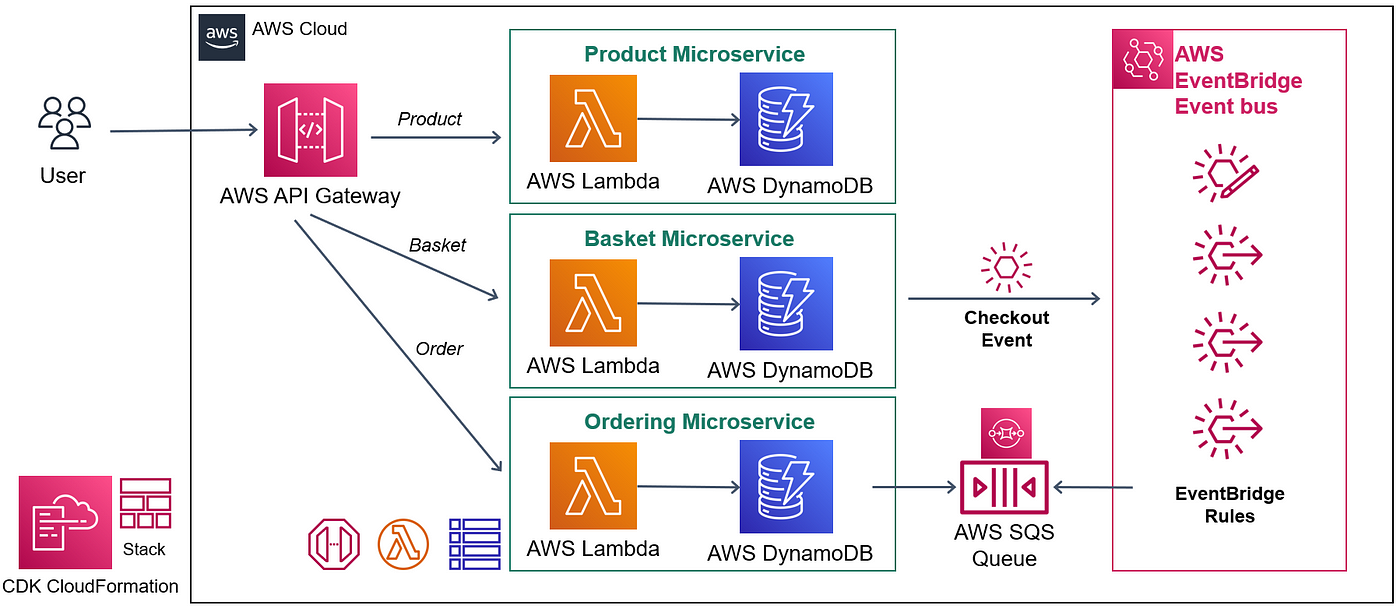













.jpg?ixlib=gatsbyFP&auto=compress%2Cformat&fit=max&q=50)





0 Response to "44 aws best practices"
Post a Comment